Picos Persistent Compute Objects, or picos, are tools for modeling the Internet of Things.
KRL Rulesets execute inside a persistent compute object, or pico.
While rulesets are the primary organizing feature of KRL, you cannot program KRL without understanding picosA pico represents an entity–something that has a unique identity and a long-lived existence. Picos can represent people, places, things, organizations, and even ideas.
Picos are:
- persistent: They exist from when they are created until they are explicitly deleted. Picos retain state based on past operations.
- unique: They have an identity that is immutable. While attributes of the pico, its state, may change, its identity does not.
- online: They are available on the Internet and respond to events and queries.
The Pico System
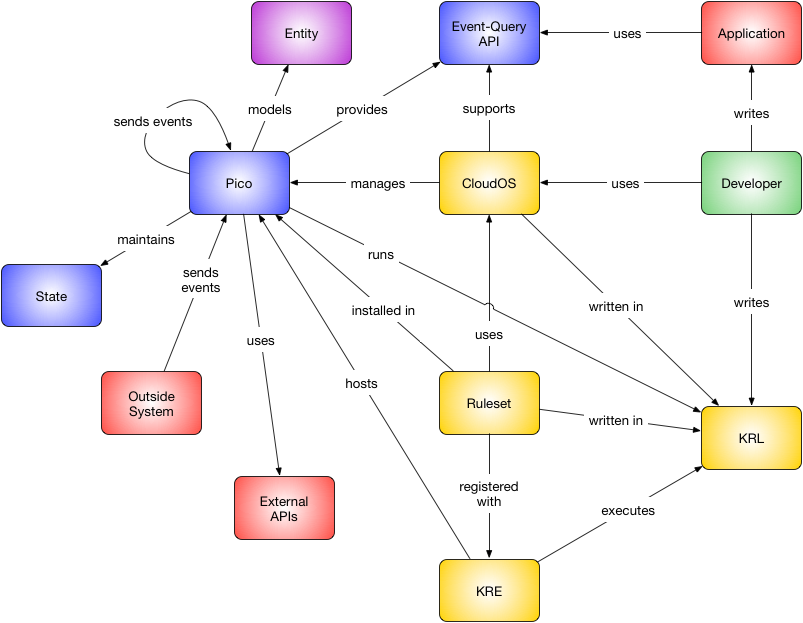
Picos exist in a system, called the "pico system." The following diagram shows the relationship and interactions between a pico and all the other members of the pico system.
KRL Rulesets execute inside a persistent compute object, or pico.
While rulesets are the primary organizing feature of KRL, you cannot program KRL without understanding picos.
Picos provides a number of important services that create the execution environment for rules:
- Identity—picos represent a specific entity and KRL rulesets execute within the context of that identity
- Storage—picos persistently encapsulate both structured and unstructured data
- Open event network—picos provide an event network:
- As rulesets are installed and uninstalled, the salience of an event for different rules in the ruleset is automatically recorded.
- The salience graph is used to automatically route events and schedule rules for execution
- Processing—picos run a unique set of rules based on the rulesets that have been installed
- Event Channels—picos have communication channels that connect them to other picos and external programs
- Authorization—picos manage authorization and access control for rulesets.
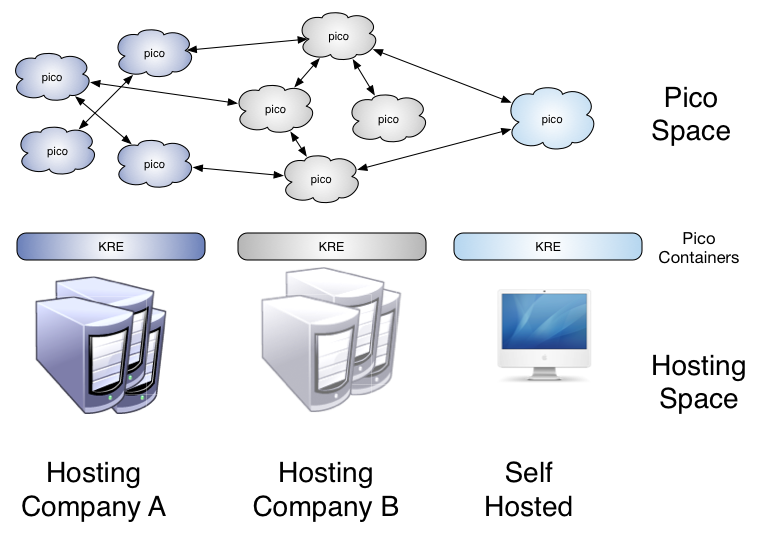
Pico Hosting Model
The Evert Query API
Event Loops
Each pico presents an event loop that handles events sent to the pico according to the rulesets that are installed in it. The following diagram shows the five phases of event evaluation. Note that evaluation is a cycle like any interpreter. The event represents the input to the interpreter that causes the cycle to happen. Once that event has been evaluated, the pico waits for another event.
...